Call Us
WithSecure Elements EDR
See attacks. Stop them.
More tools, a smaller team and complex needs: Use a single pane of glass to see and secure your company.
WithSecure's industry-leading endpoint detection and response (EDR) solution gives you contextual visibility into your security. With the automatic advanced threat identification, your IT team or managed service provider can detect and stop targeted attacks quickly and efficiently.

Product overview
When threats go unnoticed, they can't be stopped.
With breaches now taking over 220 days on average to be detected, proactive visibility is essential to keep your business secure.
Rapid and effective action is crucial once an incident is uncovered. WithSecure™ Elements Endpoint Detection and Response (EDR) enhances the threat detection and prevention features of Elements Endpoint Protection (EPP), equipping your team with the intelligence and tools needed to respond quickly.
While EPP acts as your first layer of defense by blocking known threats, Elements EDR monitors for attacks that manage to bypass initial defenses and provides clear, guided steps for remediation – all accessible from a unified console.
You gain access to advanced detection capabilities, contextual data, threat investigation, response workflows, and even proactive threat hunting – seamlessly integrated within the Elements platform.
And when you face complex threats or critical cases, you can escalate directly to WithSecure or Inter Engineering experts for hands-on help from top-tier cybersecurity professionals.
As a key part of the broader WithSecure Elements cloud ecosystem, EDR works alongside tools for vulnerability assessment, automated patching, threat intelligence, and continuous behavioral monitoring.
How does it work?
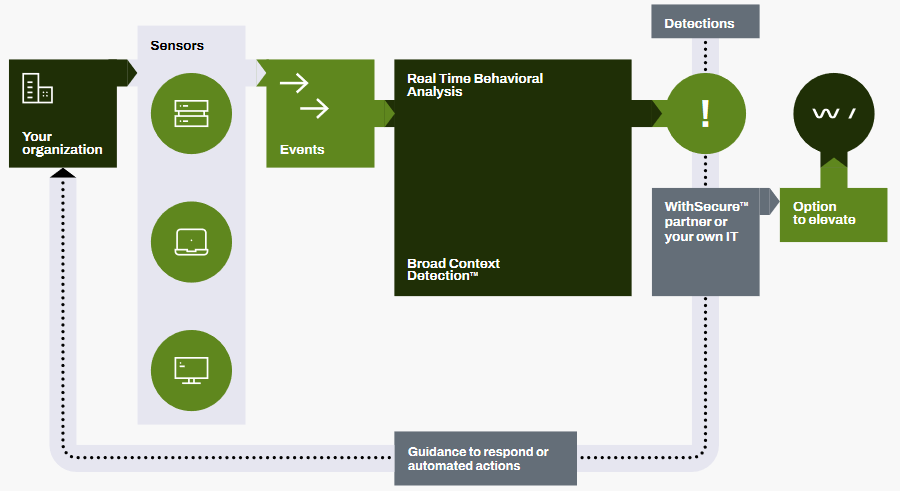
- Lightweight sensors monitor your endpoint users' behavior and stream the events to WithSecure cloud in real-time.
- WithSecure's real-time behavioral analytics and Broad Context Detection distinguish malicious behavior patterns and identify real attacks.
- Visualized broad context and descriptive attack information make confirming a detection easy. WithSecure Partner or your own IT team manages the alerts, and there's an option to elevate tough investigations to WithSecure.
- Following a confirmed detection, the solution provides advice and recommendations to guide you through the necessary steps to contain and remediate the threat.
Elements EDR key benefits
Gain automated threat detection and contextual awareness across your entire environment—not just individual endpoints. With Broad Context Detections (BCD), you get a clear timeline of attack activity, enabling you to spot patterns, analyze events, and take effective action based on expert recommendations from WithSecure. The system leverages real-time behavioral monitoring, reputation analysis, and large-scale data analytics combined with machine learning to evaluate detections in context. It helps you understand not only the technical indicators but also the severity, asset importance, and evolving threat trends across your network.






Why do you need EDR?
Why is adding EDR to your company’s EPP so important?
Ellie Ments explains it all! Watch WithSecure’s latest video to discover how managing your cybersecurity from a single, easy-to-use portal can simplify your life and boost your defense against threats.
Resources
Try it out
Get a FREE 30-day trial
Try Elements for 30 days, with no strings attached. You get instant access to our award-winning Endpoint Protection and Endpoint Detection and Response solutions.
Here’s what to expect from our leading cybersecurity service:
-
Quick installation with step-by-step guidance
-
Around-the-clock protection for all your devices against malware
-
Real-time visibility into your IT environment and security status
-
An all-in-one platform designed to strengthen your security posture
Complete the form and we'll get back to you. Don't hesitate — contact us now!
