Call Us
SSH Universal Key Manager
Centralize and automate your key management with Zero Trust
Secure your business with a proven Zero Trust key(less) management solution. Discover and manage all your SSH keys and accounts to mitigate risks. Reduce complexity with automation features. Never fail an IT audit again due to unmanaged SSH keys.

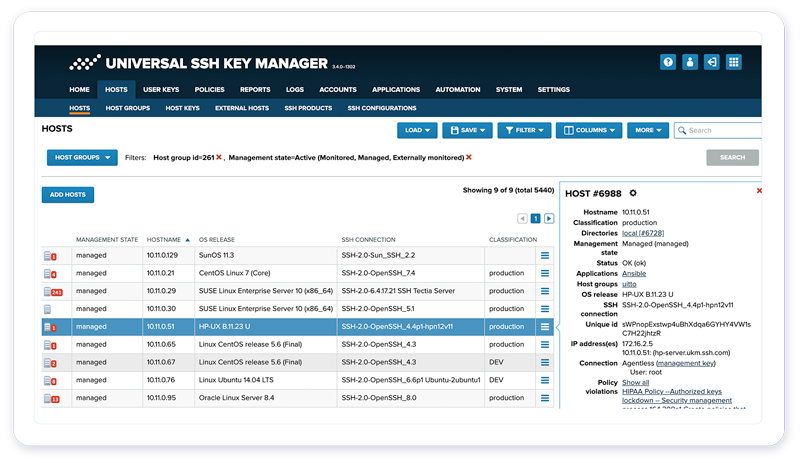
1. Eliminate SSH key risks and attack vectors
SSH keys are complex and can easily go unmanaged. These unmanaged SSH keys are then highly sought after by malicious actors.
With UKM, you remove security risks caused by ungoverned keys that might look legitimate to your existing security controls.
2. Centralize & automate SSH key lifecycle management
By default, SSH key management is decentralized and complex.
With UKM, you manage and discover all authentication keys, key configurations, and SSH login files in a centralized, universal SSH key manager. You can also automate SSH key processes, like provisioning, rotation, remediation, etc.
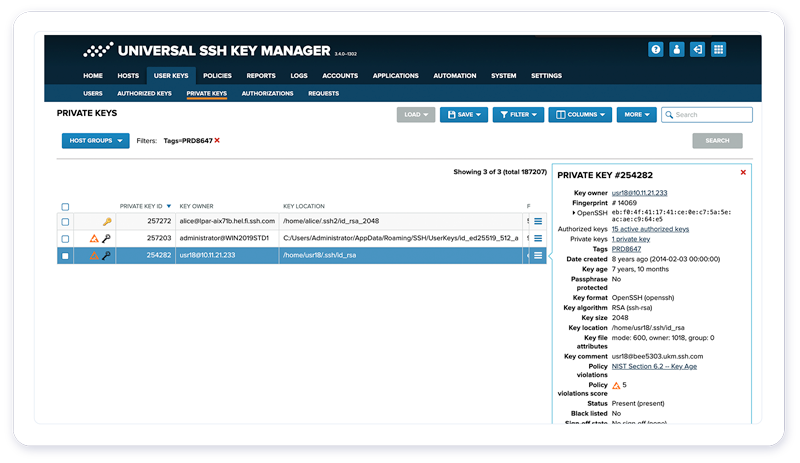
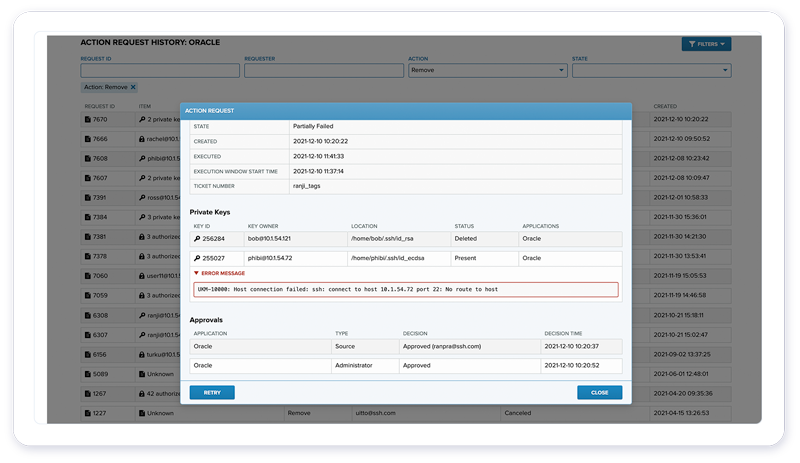
3. Secure and track your encrypted M2M connections
Machine-to-machine connections are not managed by PAM tools. You need a centralized SSH key management tool, like UKM, to manage your M2M connections, automate routines, track machine credentials, and audit all automated sessions.
UKM also ensures that all M2M connections meet your security policies and use compliant encryption standards and protocol versions.
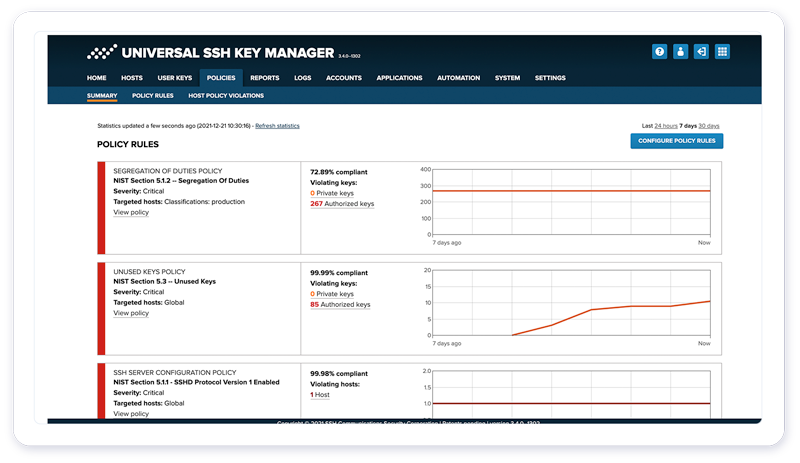
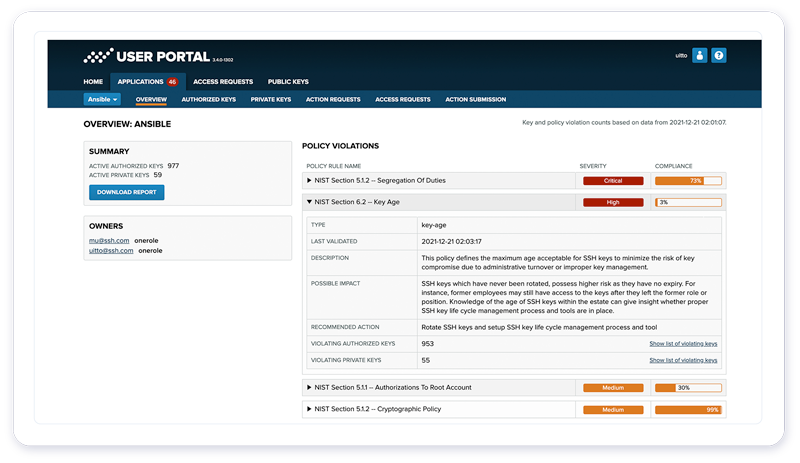
4. Enforce security policies and pass IT audits
UKM warns you about SSH keys that violate your policies, contravene regulations, or are used ungoverned. You can upgrade, rotate, and delete outdated keys with the option to reverse any action.
With UKM, you enforce compliant access control policies throughout your entire organization.
5. Reduce complexity with Zero Trust keyless access
With UKM, you can maximize key lifecycle automation and radically reduce the number of SSH keys in your environment.
UKM grants only just enough access (JEA), just-in-time (JIT), and with the least privilege needed to get the job done - without leaving any SSH keys behind to manage.
6. Choose zero-touch SSH access governance
UKM makes it easy to manage your SSH keys. You can manage authentication keys in their native locations without complicated vaulting onboarding processes.
UKM comes with non-intrusive deployment without changes to the SSH configuration files, your existing key architecture, or application code.


 Discover
Discover